Investigation
The Machine That Sees Everything
How Europe Builds Mass Surveillance Under the Banner of Child Protection
On October 14, 2025, European ministers gathered to vote on legislation bearing an unassailable title: “Regulation to Prevent and Combat Child Sexual Abuse.” Who could oppose protecting children? Yet beneath this humanitarian shield lies something else entirely—a technical architecture designed to scan every message, photograph, and video before encryption. The contradiction sits at the heart of what critics call Chat Control: a proposal that presents itself as targeted law enforcement but functions as universal population monitoring. Most revealing detail: government and military communications remain exempt from scanning. Privacy, apparently, is a right reserved for those who write the laws, not those who live under them. The Danish presidency pushed hard for passage, but Germany’s last-minute opposition formed a blocking minority. The proposal lives on, waiting for another attempt. What Europe decides shapes global precedent—once this infrastructure exists, it cannot be unbuilt.
The Mathematics of False Accusation
Client-side scanning sounds technical but works simply: software examines content on your device before encryption happens. Think of it as opening every letter, photographing the contents, then sealing the envelope. Technically, encryption remains intact. Functionally, it becomes theater. Over 500 cryptography scientists state this approach “inherently undermines” encryption’s protections.
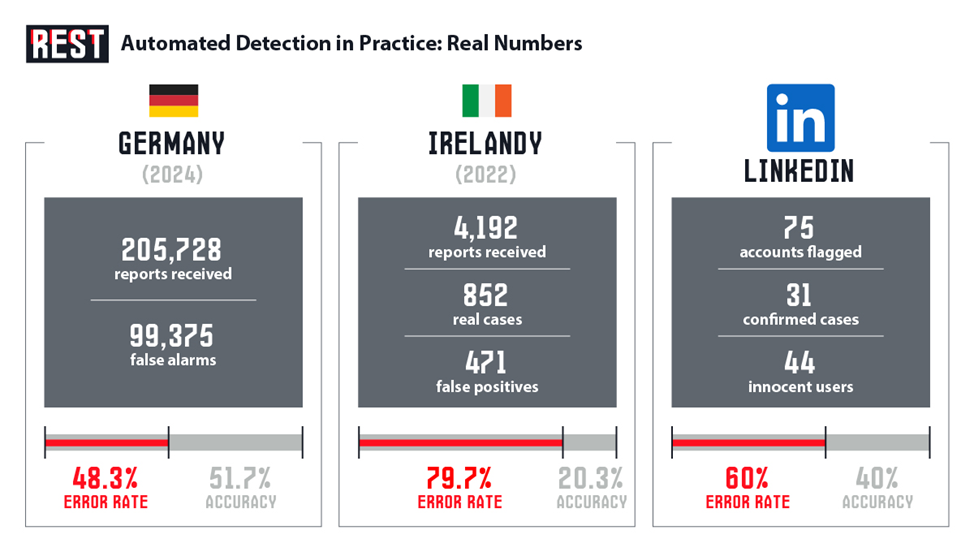
But the deeper problem is mathematical. Germany’s Federal Criminal Police Office reported that in 2024, 99,375 reports—nearly half of all tips received—were false alarms. An error rate of 48.3%. These aren’t abstract statistics. Each number represents someone’s family photograph flagged as criminal evidence, forwarded to authorities, investigated. In Ireland, only 20.3% of automated reports involved actual illegal material. LinkedIn’s PhotoDNA implementation—the technology lawmakers recommend—produced nearly 60% false positives.
Scale this to mandatory scanning of billions of daily messages across encrypted platforms. Even a 1% error rate generates millions of false accusations. Dutch police already stated they lack capacity to handle the expected volume. The system wouldn’t enhance child protection—it would bury genuine cases under algorithmic noise while criminalizing innocent citizens whose vacation photos trigger pattern-matching suspicion.

The Hollywood Lobby: Thorn’s European Campaign
In May 2022, days before unveiling her proposal, EU Commissioner Ylva Johansson wrote to Thorn—a California organization co-founded by actors Ashton Kutcher and Demi Moore. Her letter read: “We have shared many moments on the journey to this proposal. Now I am looking to you to help make sure that this launch is a successful one.” Not advice from technical experts. Not consultation with privacy advocates. Active coordination with a foreign lobbying organization that sells the very scanning software the proposal would mandate.
Thorn registers as a charity in EU lobby databases. Yet it sells commercial AI tools—the US Department of Homeland Security alone has purchased $4.3 million in software licenses since 2018. Thorn spent €630,000 on lobbying in 2022, meeting with Commission President Ursula von der Leyen, multiple commissioners, and key digital policy officials.
The network extends beyond Silicon Valley celebrities. WeProtect Global Alliance—which emerged from governmental initiatives co-founded by the Commission and the United States—transformed in April 2020 into a “foundation” registered at a residential address in the Netherlands. Its board includes government representatives, security agencies, Big Tech companies, and a senior Commission official heading the anti-CSAM team. When a Europol officer transferred to Thorn in 2022, continuing his Europol work for two months, the EU Ombudsman ruled it “maladministration”—the agency had failed to consider conflict of interest risks.
Meanwhile, Johansson repeatedly claimed in Swedish interviews that encrypted communications could be scanned without breaking encryption. When pressed by journalists about whether source protection would survive Chat Control, her responses revealed fundamental technical misunderstanding. She later discussed extending the system to drug crimes—confirming what internal documents already showed: Europol officials suggesting “other crime areas” would benefit from detection capabilities.

Germany’s Calculated Ambiguity and Denmark’s Offensive
Germany’s position exposed how institutional pressure operates behind closed doors. The country opposed Chat Control throughout 2024, citing historical experience with surveillance states. In September 2025, Germany joined opposition alongside Luxembourg and Slovakia. Days later, under Danish presidency maneuvering, Germany mysteriously reverted to “undecided” status.
As the October 14 vote approached, German ministries—Interior, Justice, Family, Digital—maintained stone wall silence. No disclosure of position despite imminent decision. Patrick Breyer documented that during September 12 negotiations, Denmark claimed the European Parliament would refuse to extend voluntary scanning if the Council didn’t agree—a claim Breyer proved factually false, calling it “blatant manipulation.”
Then, on October 7, German Justice Minister Stefanie Hubig announced Germany would not agree to Chat Control. The CDU/CSU parliamentary group stated: “We are opposed to the unwarranted monitoring of chats. That would be like opening all letters as a precautionary measure.” With Germany’s 83.5 million citizens representing 19% of EU population, this opposition became decisive for blocking minority formation.
Meanwhile, Denmark weaponized its rotating presidency. Justice Minister Peter Hummelgaard stated at a July press conference: “We must break with the totally erroneous perception that it is everyone’s civil liberty to communicate on encrypted messaging services.” Not a slip of the tongue—an explicit ideological position denying privacy as fundamental right. The Danish text mandated scanning for “unknown” content using AI, not just hash-matching against known databases. Government and military accounts received explicit exemption—creating two-tier privacy where state actors retain security while citizens face universal monitoring. Prime Minister Mette Frederiksen threw considerable political capital at the initiative, making its passage her presidency’s defining objective.

The Market Exodus and Legal Collision
Signal Foundation President Meredith Whittaker stated unequivocally: “If we were given a choice between building a surveillance machine into Signal or leaving the market, we would leave the market.” She calls the proposal’s effect comparable to “malware on your device”—scanning everything before encryption, creating vulnerabilities exploitable by hostile actors.
Tuta (formerly Tutanota), a German encrypted email provider, announced it would pursue legal action if the proposal passes: “We will do whatever it takes to ensure your right to privacy.” WhatsApp previously threatened withdrawal from the UK over similar demands. The pattern is consistent: privacy-focused platforms cannot comply without destroying their technical foundations.
This creates market distortion. Meta, Google, Microsoft—already scanning unencrypted communications voluntarily—face minimal operational changes. European privacy-by-design alternatives become legally untenable. The regulation demands implementation impossible for open, federated European systems while granting structural advantages to centralized US tech giants. So much for digital sovereignty.
The legal collision is equally stark. The Council of the European Union’s Legal Service criticized the proposal for violating fundamental rights to private life and data protection, referencing Court of Justice rulings against generalized data retention. The European Data Protection Supervisor warned the proposal “could become the basis for de facto generalized and indiscriminate scanning.” In February 2024, the European Court of Human Rights ruled requiring degraded encryption “cannot be regarded as necessary in a democratic society.”
Yet legal barriers haven’t stopped advancement. Denmark drafted procedural decorations—court orders, oversight bodies, auditing requirements—attempting to circumvent constitutional obstacles. But the architecture remains: mandatory scanning of everything on devices, regardless of judicial decoration.

Conclusion: The Infrastructure Awaits
The October 14 vote didn’t happen. Germany’s opposition, combined with resistance from Austria, Belgium, Czech Republic, Finland, Luxembourg, Netherlands, Poland, and Slovakia, prevented qualified majority. But the proposal remains active. Supporters can reintroduce modified versions. The infrastructure they envision—once built—cannot be unbuilt.
Chat Control represents an architectural decision about digital society’s fundamental structure. The choice is binary: either communications remain private by technical design, or they become transparent to state monitoring by mandatory implementation. There exists no middle ground. Client-side scanning either exists or it doesn’t. Encryption either protects or it doesn’t.
Scientists confirm perpetrators can evade detection with “trivial technical modifications,” while the system generates mass false accusations against innocents. The proposal wouldn’t meaningfully protect children. It would normalize universal monitoring while creating cybersecurity vulnerabilities exploitable by the very actors it claims to combat.
The lobby network remains intact. Thorn continues operations. WeProtect maintains board memberships. Commission officials who coordinated the proposal’s drafting retain positions. Commercial interests aligned with law enforcement agencies generate permanent pressure toward surveillance expansion. The machine that sees everything, once built, serves whoever controls it. In a continent that remembers what surveillance states can do, this should require no explanation. Yet the vote approaches again, and the architecture awaits construction.























